- Distribution Method : Automatic infection using exploit by visiting website
Initial samples demonstrate that Magniber only targets Korean-speaking users and, if it does not detect Korean language on the infected system, it will terminate its processes and not encrypt any files. If it does detect the Korean language, it will search for files to encrypt and append either. Kgpvwnr, or.dxjay to the file names. Clone via HTTPS Clone with Git or checkout with SVN using the repository’s web address.
Ahnlab Magniber Decrypt V4
- MD5 : d410ad89fe5e0350e648ac39308fd848
Ahnlab Magniber Decrypt V4.1
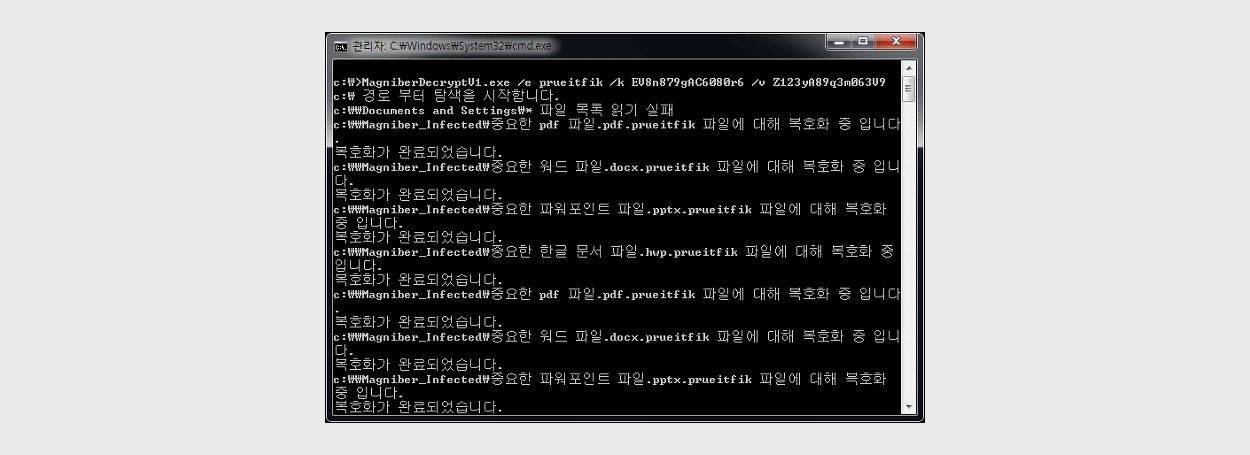
- Major Detection Name :Trojan/Win32.Magniber.R215116 (AhnLab V3), Trojan.Win32.MyRansom.131072 (ViRobot)
- Encrypted File Pattern : .ypail
- Malicious File Creation Location :
- C:Users%UserName%AppDataLocalREAD_FOR_DECRYPT.txt
- C:Users%UserName%AppDataLocalypail.exe
- C:Users%UserName%Desktop<Random>.exe
- C:WindowsSystem32Tasksypail
- C:WindowsSystem32Tasks<Random>
- C:WindowsSystem32Tasks<Random>1
- Payment Instruction File : READ_ME_FOR_DECRYPT.txt

- Major Characteristics :
- Offline Encryption
- Only run on Korean operating system
- Change the default values of the registry entry 'HKEY_CLASSES_ROOTmscfileshellopencommand' and disable system restore (wmic shadowcopy delete) using Event Viewer (eventvwr.exe)
- Auto execute ransomware (pcalua.exe -a C:Users%UserName%AppDataLocalypail.exe -c <Random>) and payment instrucition file (%LocalAppData%READ_FOR_DECRYPT.txt) every 15 minutes by adding Task Scheduler entries
- Auto connect MY DECRYPTOR site (cmd.exe /c start iexplore http://<URL>) every a hour by adding Task Scheduler entries